DHCP
Dynamic Host Configuration Protocol (DHCP) is a network protocol that is used to automatically assign and manage IP addresses and other network configuration information to devices on a network. DHCP eliminates the need for administrators to manually assign static IP addresses to each device on a network, which can be time-consuming and prone to errors.
Here's how DHCP generally works:
DHCP Server: A DHCP server is a computer or device on the network that is configured to provide dynamic IP addresses to devices on the same network. This server typically has a pool of available IP addresses to assign to devices.
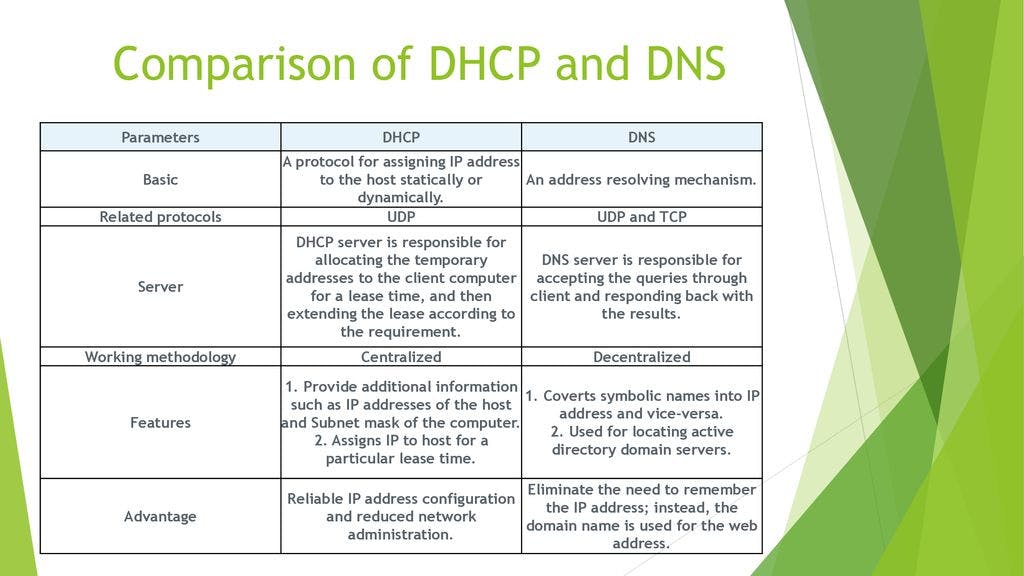
DHCP Discover: When a device (such as a computer, smartphone, or printer) connects to a network, it sends out a DHCP Discover message to discover DHCP servers on the network. This is usually broadcasted as a request for an IP address.
DHCP Offer: DHCP servers that receive the DHCP Discover message respond with a DHCP Offer. The offer includes an IP address that the server is willing to lease to the device and other configuration information such as the subnet mask, default gateway, and DNS server addresses.
DHCP Request: The device selects one of the DHCP server offers and sends a DHCP Request message to the chosen server, confirming its request for the offered IP address.
DHCP Acknowledgment: The DHCP server responds with a DHCP Acknowledgment, indicating that the device is allowed to use the requested IP address. The server also provides the lease duration, which is the time the device is allowed to use the assigned IP address.
IP Configuration: The device configures its network interface with the assigned IP address, subnet mask, default gateway, DNS server, and other relevant information received from the DHCP server.
Lease Renewal: Periodically, the device may request a lease renewal from the DHCP server to continue using the assigned IP address. If the device is no longer connected to the network or if the lease expires, the IP address is released back to the DHCP server for reuse.
DHCP simplifies network administration and ensures efficient use of IP addresses by dynamically allocating them as needed. It is commonly used in local area networks (LANs) and is an essential component of most residential and business networks.
Advantages of DHCP:
Automated Configuration: DHCP automates the process of assigning IP addresses to devices on a network, eliminating the need for manual configuration. This automation simplifies network administration, reduces the risk of human errors, and ensures that devices can easily connect to the network without requiring manual intervention.
Efficient Resource Utilization: DHCP allows for dynamic allocation of IP addresses from a pool, facilitating efficient use of available addresses. Devices receive temporary leases, and when they disconnect or are no longer in use, their IP addresses are released back to the pool for other devices to use. This dynamic allocation reduces the likelihood of IP address conflicts and optimizes address utilization.
Centralized Management: DHCP centralizes the management of IP address assignments. Network administrators can configure and monitor IP addresses, subnet masks, and other configuration parameters from a central DHCP server. This centralization streamlines network management, making it easier to maintain and troubleshoot the network infrastructure.
Disadvantages of DHCP:
Dependency on DHCP Server: DHCP relies on the availability and proper functioning of DHCP servers. If the DHCP server is unavailable or experiences issues, devices may struggle to obtain IP addresses, leading to connectivity problems. Redundancy measures or backup DHCP servers are often necessary to mitigate the risk of service disruptions.
Security Vulnerabilities: The trust relationship between DHCP servers and clients can be exploited by malicious actors. Rogue DHCP servers may distribute incorrect or harmful configuration information, posing security risks to the network. Implementing security measures such as DHCP snooping is essential to prevent unauthorized DHCP server activity and mitigate potential security vulnerabilities.
Potential for IP Address Exhaustion: In environments with a limited pool of available IP addresses and long lease durations, there is a risk of IP address exhaustion. If the number of devices in the network exceeds the available addresses, it can lead to connectivity issues. Proper planning, monitoring, and potentially adjusting lease durations are necessary to avoid this problem.
DNS
Domain Name System (DNS) is a fundamental protocol used on the Internet to translate human-readable domain names into IP addresses. Here are three key points regarding DNS:
Name Resolution:
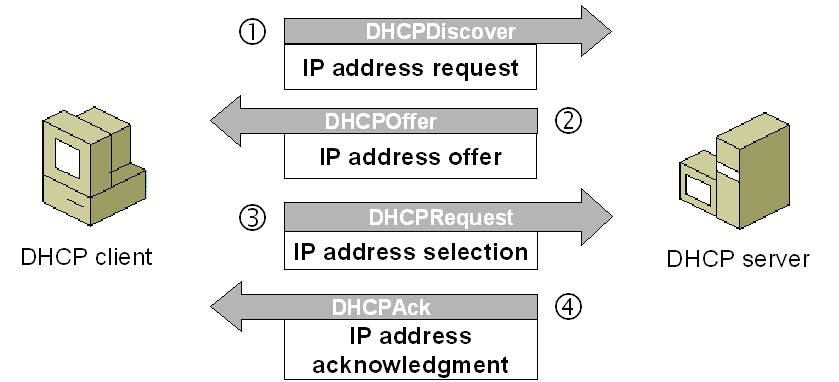
Translation of Domain Names to IP Addresses: DNS serves as a distributed database that translates human-readable domain names into numerical IP addresses (such as 192.168.1.1). This translation is essential for network communication because computers communicate using IP addresses, while humans find it easier to remember domain names.
Hierarchical Structure: DNS has a hierarchical structure, organized in a tree-like fashion. The top level is the root domain, followed by top-level domains (TLDs) like .com, .org, and country-code TLDs (e.g., .us, .uk). Beneath the TLDs, there are second-level domains (SLDs) and subdomains, forming a structured naming system.
Name Resolution Process:
DNS Query Process: When a user enters a domain name into a web browser or any network-aware application, the system initiates a DNS query to resolve the domain to an IP address. The DNS query starts locally on the user's device and may involve multiple DNS servers in a recursive process until the final authoritative DNS server is reached.
Caching Mechanism: DNS employs a caching mechanism to store previously resolved domain-to-IP mappings. This helps improve the efficiency of subsequent queries by reducing the need to repeatedly traverse the entire DNS hierarchy for frequently accessed domains. Caching occurs at various levels, including on the user's device, local DNS servers, and even higher-level DNS servers.
DNS Records and Types:
Resource Records (RRs): DNS databases store information in resource records, which contain various types of data associated with domain names. Common types include:
A (Address) Record: Maps a domain to an IPv4 address.
AAAA (IPv6 Address) Record: Maps a domain to an IPv6 address.
MX (Mail Exchange) Record: Specifies mail servers responsible for receiving email on behalf of a domain.
CNAME (Canonical Name) Record: Provides an alias for another domain name.
Name Servers and Zones: DNS is distributed across multiple servers. Each domain is associated with authoritative name servers responsible for storing and providing information about that domain. A zone is a contiguous portion of the DNS namespace, and name servers manage specific zones.
DNSSEC (DNS Security Extensions): DNSSEC adds a layer of security to DNS by incorporating digital signatures into DNS responses. This helps prevent certain types of cyber attacks, such as DNS spoofing or cache poisoning, by ensuring the integrity and authenticity of DNS data.
DNS plays a critical role in the functionality of the Internet, enabling users to access websites, send emails, and interact with various online services using human-readable domain names.
Advantages of DNS:
User-Friendly Naming System: DNS provides a human-readable naming system, allowing users to access websites and services using easily memorable domain names instead of numerical IP addresses. This enhances the user experience by simplifying the process of navigating the internet.
Dynamic IP Address Management: DNS allows for dynamic management of IP addresses. As the IP addresses of servers or services change, administrators can update DNS records to reflect these changes. This flexibility is crucial in dynamic environments where IP addresses may be reassigned or changed frequently without impacting user accessibility.
Load Balancing and Redundancy: DNS supports load balancing by distributing incoming traffic among multiple servers. This enhances performance and ensures high availability of services. Additionally, DNS can be configured to provide redundancy, directing traffic to alternative servers in case of a failure, and improving overall system reliability.
Disadvantages of DNS:
DNS Spoofing and Cache Poisoning: DNS is vulnerable to attacks like DNS spoofing and cache poisoning, where malicious actors provide false DNS information. This can lead users to fraudulent websites or compromise data integrity. While DNSSEC aims to address these vulnerabilities, not all systems implement it, leaving room for security concerns.
Dependency and Single Point of Failure: DNS creates a dependency on its infrastructure, and if it experiences issues or becomes unavailable, users may face difficulties accessing websites and services. The centralized nature of DNS poses a potential single point of failure. Redundancy measures, such as deploying multiple DNS servers in different locations, can mitigate this risk.
Propagation Delays: Changes made to DNS records, such as updates to IP addresses or the addition of new domains, undergo propagation across the global DNS infrastructure. During this propagation period, users in different locations may experience inconsistencies in DNS resolution. While these delays are typically short, they can impact the timely implementation of changes and DNS updates.
While DNS provides critical functionality for internet communication, addressing these disadvantages through security measures, redundancy, and ongoing protocol enhancements is essential for maintaining a secure and reliable naming system.